What data recovery tools to buy if you want to start a data recovery business?
Free video data recovery training on how to recover lost data from different hard drives?
Where to buy head and platter replacement tools at good prices?
Data recover case studies step by step guide
I want to attend professional data recovery training courses
Windows XP, 2000 and Server 2003 have introduced a way to protect your information from unauthorized access. Fully integrated into the Windows Explorer shell, EFS or the Encrypting File System uses a combination of symmetrical and public/private key encryption to secure data that is stored in NTFS partitions.
Technically, it uses the DESX or Data Encryption Standard X algorithm to encrypt data. EFS helps to counter the vulnerability found in the NTFS ACL, whereby protected data can be accessed when the attacker gains physical possession of the computer with the exploitation of third party recovery software.
HOW DOES EFS WORKS?
The first time you perform an encryption, EFS will automatically generate a public key pair and file encryption certification.
A random generated key called the File Encryption Key (FEK) encrypts the data. This FEK is then encrypted with the EFS public key which is also stored along with the encrypted file.
The private key which resides within the user’s profile is used to decrypt the FEK which in turn decrypts your data. Each time you open an encrypted file, EFS will search the system’s key store for a file encryption key.
When an unauthorized personnel tries to open an encrypted file, an Access Denied error message will be displayed. Copying a regular file into an encrypted folder will render the file encrypted. Doing the reverse will still maintain its encryption status.
All the time, the encryption and decryption of data is done “on the fly” without even noticed by the user. If set up properly, even a system administrator will not be able to “peep” the data as the data access is no longer depending on conventional Windows file security attributes.
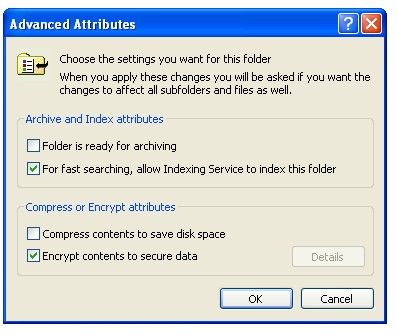
To encrypt or decrypt a folder, follow these steps:
1. Right click on the folder to be encrypted and select Properties
2. On the General tab of the Properties dialog box, click Advanced
3. Select the option to Encrypt Contents To Secure Data and click OK
To decrypt, simply clear the Encrypt Contents To Secure Data checkbox.
Click OK in the Encrypted Files Properties dialog box
When EFS encrypts a file, the following occurs:
* A symmetric key or File Encryption Key (FEK) is generated
* System uses the FEK and DESX algorithm to create the encrypted file
* FEK is encrypted using the user’s public key
* Both keys are attached to the encrypted file in a special field called the data decryption field
Note:
1. Export and Saved Your Keys
To fully secure your encrypted data, you are advised to export your private key and certificates to a removable drive when the workstation is not in use. When you need to decrypt the file, restore the private key back into the workstation. See Backup Certificates & Private Key of Encrypting File Systems.
2. Encrypt Folders Instead
It is recommended to encrypt a folder rather than individual files. To decrypt all files under the folder, you just need to select a single folder.
3. Designate Recovery Agents
Windows allow you to set up a recovery agent accounts to provide means for data recovery in case you lose your primary key, without which your data may no longer be accessible.
Data recovery Salon welcomes your comments and share with us your ideas, suggestions and experience. Data recovery salon is dedicated in sharing the most useful data recovery information with our users and only if you are good at data recovery or related knowledge, please kindly drop us an email and we will publish your article here. We need to make data recovery Salon to be the most professional and free data recovery E-book online.







1 Comment
i don’t no how does work on EFS and FEK still
and thanks for the given information.
thanks